Security
The world’s leading law firms trust Legatics
We’ve built Legatics to the highest security standards and provide industry-leading permissions to customise the security of each transaction.

Cloud security
Security, compliance, and privacy are built-in
Legatics’s cloud-native architecture is built on top of Amazon Web Services. This, together with the use of third party tools such as Cloudflare and Datadog, ensures network security, resilience, transparency, and reliability.
Application security
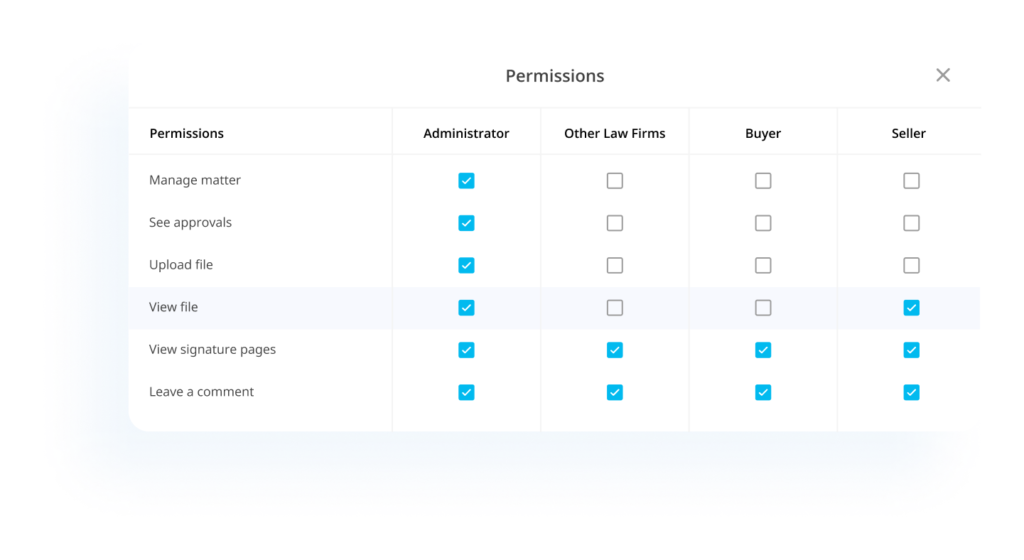
Matter security is in your control
Legatics’s platform is built to enable you, and your users, to have granular control over who can access matters and who can see information inside those matters.

Data security
Protecting your data is our priority
Legatics takes data security extremely seriously. We take every step possible to ensure that all user data is secure.
Organisation security
Security is our passion
Security at Legatics extends beyond systems and technologies. It’s also embedded into our organisational culture and everyday business processes.

This is the tip of the iceberg
Book a demo to learn more about how we secure your transactions.


