Security
The world’s leading law firms trust Legatics
We’ve built Legatics to the highest security standards and provide industry-leading permissions to customise the security of each transaction.

Cloud security
Security, compliance, and privacy are built-in
Legatics’s cloud-native architecture is built on top of Amazon Web Services. This, together with the use of third party tools such as Cloudflare and Datadog, ensures network security, resilience, transparency, and reliability.
Web application firewall
Cloudflare’s WAF filters and inspects web traffic, blocking malicious requests to protect against DDoS and other threats.
Web application firewall
Cloudflare’s WAF filters and inspects web traffic, blocking malicious requests to protect against DDoS and other threats.
Web application firewall
Cloudflare’s WAF filters and inspects web traffic, blocking malicious requests to protect against DDoS and other threats.
Application security
Matter security is in your control
Legatics’s platform is built to enable you, and your users, to have granular control over who can access matters and who can see information inside those matters.
SAML SSO and Two-Factor Authentication (2FA)
Control who can access Legatics. For details about our SSO providers, click here.
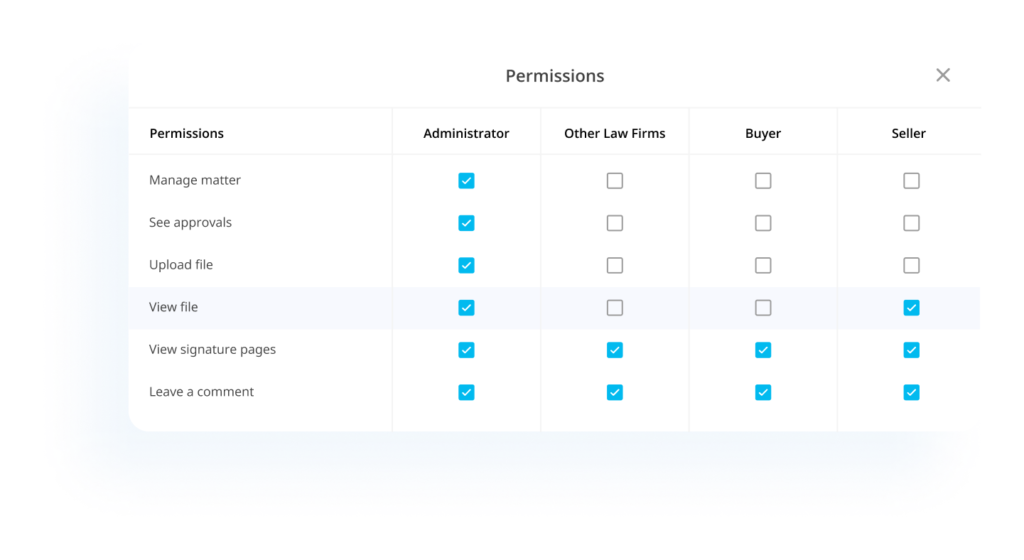
Comprehensive user permissions
Role-Based Access Control (RBAC) allows you to customize who can view, edit, or manage your matters, with fine-tuned permissions for each user.
Audit trail
Record user actions for everyone.

Data security
Protecting your data is our priority
Legatics takes data security extremely seriously. We take every step possible to ensure that all user data is secure.
Data encryption
All data uploaded to Legatics is encrypted at rest with AES-256 bit encryption – and all requests must be made over HTTPS using TLS v1.2 or higher.
Data separation
Each customer has their own tenancy, with the data logically separated from data in another customer’s tenancy.
BYOK (Bring Your Own Key)
As an advanced security measure, customers on private instances can enable BYOK (customer-managed encryption keys) via AWS Key Management Service (KMS) for additional control over encryption keys and data.
Data hosting locations
Legatics has several core AWS hosting data locations, covering the United States, EU, Australia and more, to support our customers’ wide-ranging data requirements.
Backups
Data is backed up on an hourly, daily and monthly basis and replicated across multiple AWS availability zones to maintain resilience in case of an issue with any one zone.

Organisation security
Security is our passion
Security at Legatics extends beyond systems and technologies. It’s also embedded into our organisational culture and everyday business processes.
ISO 27001:2022
Legatics holds an ISO 27001:17 certificate issued by the British Assessment Bureau (BAB). This confirms that Legatics has been internally and externally audited for compliance with the ISO 27002 control set.
Cybersecurity community engagement
As a member of the National Cyber Security Centre’s (NCSC) Cyber Security Information Sharing Partnership (CISP), Legatics stays informed about the latest cyber threats and industry best practices.
Policies
Legatics has developed a comprehensive set of security policies, which are updated frequently and communicated to all employees.
Employee screening
Legatics performs background checks on all new employees in accordance with the laws applicable to our business.
This is the tip of the iceberg
Book a demo to learn more about how we secure your transactions.

